Biometric Authentication Technology – Everything you Need to Know

- 01 The History of Biometric Authentication
- 02 Biometric technology - Protecting global companies from Identity Theft
- 03 Some major types of Biometrics
- 04 Advantages of using Biometric technology
- 05 Use cases of Biometric Authentication
- 06 Biometric Technology fulfilling KYC/ AML regulations
- 07 Challenges of Biometric technology
- 08 Facial Biometric Verification amid Pandemic
Nowadays businesses are looking for more secure systems for the sole reason of customer authentication. Either it’s the small business, eCommerce industry, or financial sector, biometrics technology seems to be gaining attention. Biometric authentication technology has seen a lot of advancements over the past few years and is considered one of the most effective ways for customer identification.
What is Biometric Technology?
It is an automated customer recognition method for verifying the identities of individuals based on behavioral and physiological traits such as fingerprints, voice, facial features, DNA, retina, iris, and others.
Every year millions of people become victims of identity theft crimes. The Federal Trade Commission recorded 3 million reports in the previous year out of which 15% belong to identity theft, alone. Biometrics are becoming the authenticators of identity to eliminate crimes and imposters.
Customer identification through biometrics is taking over the world and is progressively more prevalent than initially anticipated. Companies are utilizing biometric technology for fraud detection and security because biometric security is way more beneficial than old and conventional identity verification methods. Apart from providing individual verification, it keeps customer data confined for authorized access only. Biometric technology is not new and has been around for hundreds of years and has seen remarkable innovations while stepping up the ladder.
The History of Biometric Authentication
Biometric authentication is considered a masterstroke in the verification market. The history of Biometric authentication dates back to the 1800s when the first biometric identification system was recorded in Paris, France. It was Alphonse Bertillon – a French police officer and biometrics researcher who devised a unique technique of identifying criminals through biological characteristics. Followed by Fingerprint identification in the 1880s by Edward Henry who instigated the Henry Classification System. Henry’s system was favored by law enforcement agencies, replacing Bertillon’s way of performing identification.
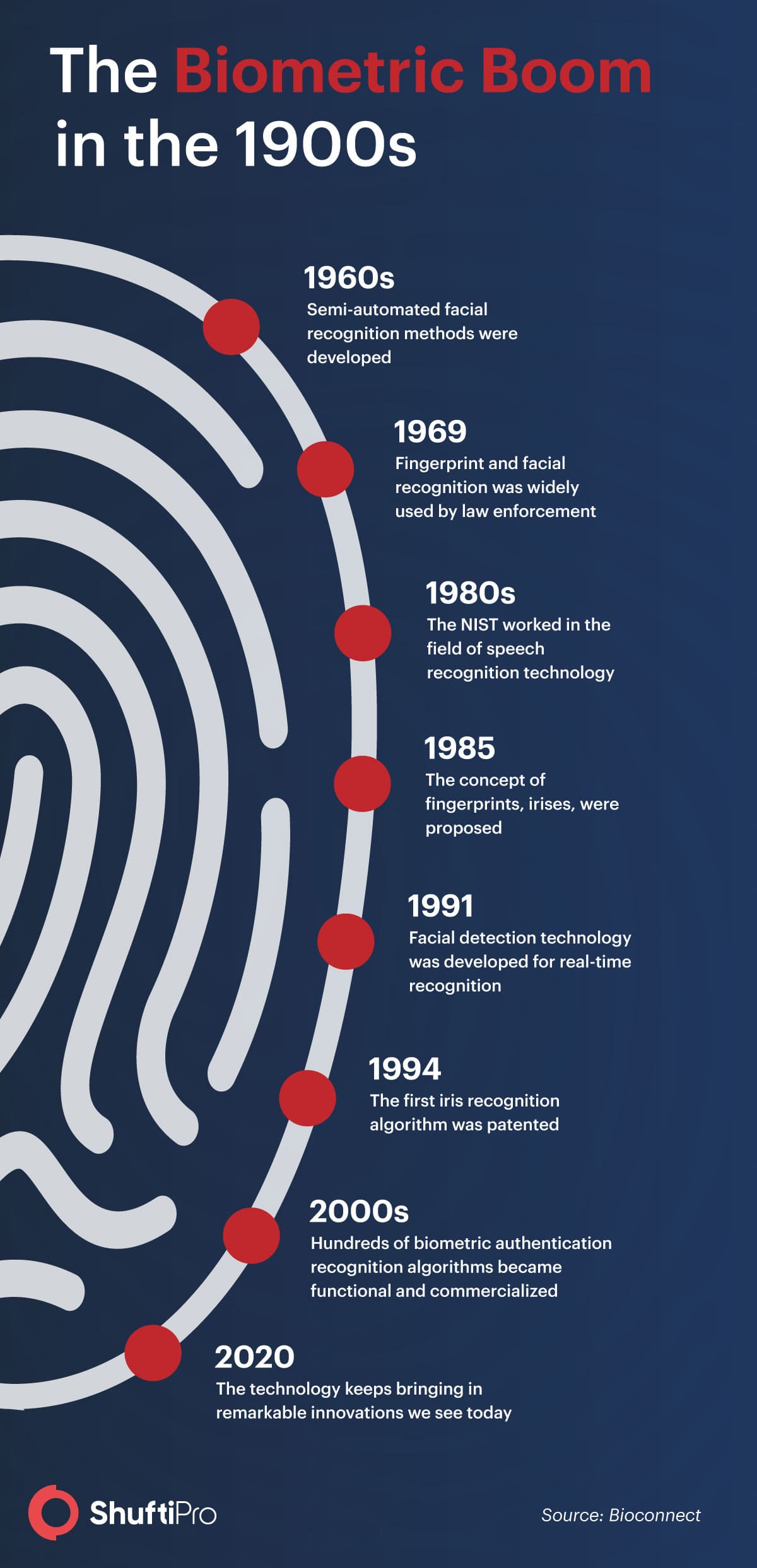
Fast-forwarding to 2020, biometric authentication technology for customer verification is advancing rapidly. It is increasingly becoming a part of everyday business operations. Many hardware/ software companies are integrating biometrics in their systems for authentication say, for example, Apple inc.
Biometric technology – Protecting global companies from Identity Theft
Global industries are using biometrics for customer authentication to eliminate identity theft and unauthorised access. The biometric industry is evolving to support businesses and effectively prevent crimes from happening in the best way possible. Over the past few years, customer identity theft has become one of the most common crimes. It takes place when identity thieves steal victims’ personal information for unauthorised financial transactions.
After stealing customer identities, they engage in illegal purchases or apply for loans in the victim’s name which is threatening to global businesses as it puts a strain on sensitive customer data and business revenues. Losses due to frauds have increased by 13% in the years 2019 to 2020 respectively. Therefore, global industries have been deploying biometric authentication systems to prevent identity theft.
Some major types of Biometrics
As mentioned above, biometrics usually fall under two categories: Biological and Behavioural biometric characteristics. Biological traits include individuals’ physiological and physical features, whereas behaviors include actions performed by individuals such as voice patterns.
Fingerprint Scanners
Fingerprints scanners have seemed to be everywhere and used by everyone. They aren’t limited to businesses but smart devices are also deploying fingerprints scanning for unlocking devices. According to Spiceworks, fingerprint scanning is the most common type of biometric authentication which is used by almost 57% of global companies. They are a type of biological biometric system as fingerprints are secured with the individual’s live participation however, it can also be collected when left on an object, this system is used by law enforcement agencies to trace criminals. But new and advanced biometric identification techniques are replacing fingerprint scanning.
Facial Biometric Recognition
In facial biometric authentication, the live presence of individuals is ensured. Just like other biometric solutions, facial recognition analyses the unique facial features of individuals and matches them with the available databases for authentication. Having said that, facial biometric authentication is considered a more convenient way of identifying criminals among the crowds. Imposter crimes are on the rise, according to FTC, they ripped $667 million last year off of Americans. So, companies understand the true capabilities of facial recognition systems, therefore it is attracting global interest.
Voice Recognition
Voice recognition is another biometric system that is extensively used for identifying and authenticating customers. According to studies, at least 2% of businesses use voice recognition to verify individuals.
Signature recognition
This includes the identification of an individual by analysing their handwriting. Signature recognition involves further two types namely, static and dynamic signature analysis. In static compares one scanned signature to either another scanned signature or ink signature. On the other hand, Dynamic signature uses behavioral characteristics that an individual displays while making a signature. Digital signature scanners are frequently used by retail stores and baking institutions.
DNA
DNA scans are primarily used by law enforcement agencies in order to identify suspects. It uses a segment of human individuals for verification purposes.
Hand geometry
Identification through hand geometry analyzes and measures the shape of an individual’s hand. This type of identification is easier to use when there are a number of users accessing the system regularly. Also, the accuracy rate is comparatively high.
Iris and retina based biometric authentication
Iris based biometric includes authentication through iris scanning. Similarly, retina-based biometric analysis of the layer of blood vessels at the back of the eye called the retina. Iris scanners can work even if the person is wearing the glasses and it’s also easier to use. On the other hand, retinal scanning is considered accurate but it does not require an individual to look at a single point for verification and also not convenient if the person is wearing glasses. Therefore Iris scanning is more widespread as compared to retinal scanning.
Additionally, biometric authentication can identify individuals through writing patterns, physical movements including the way individuals move, navigation patterns such as the movement of their fingers on mouse pads, last but not least their engagement patterns with technology.

Advantages of using Biometric technology
One of the key benefits of using biometric technology is that it is reliable and keeps the imposters away. Biometric security is enhanced, and identity can be confirmed without documents (that may be stolen or forged) on the spot in real-time. A lot of businesses are widely accepting the comprehensive applications of online biometric authentication including fingerprint ID because of its future potential.
- Biometric technology is increasingly becoming popular for ID verification, specifically within financial institutions, and government agencies for its reliability and consistency.
- Additionally, it offers higher accuracy rates. Using physical traits is advantageous for authenticating end users.
- It is considered safe because biometric traits can not be stolen or forged unless criminals go through extensive surgeries which are unlikely at times.
- Biometric technology is time and cost-effective and highly user friendly.
- Highly useful for criminal identification and forensics
- Prevents unauthorised accessing of user accounts, mobile phones, and others
- Passwords can be easily stolen or hacked. With biometrics technology, customers will not lose any data which can be used for criminal activities
- Customer can rely on biometric for making secure financial transactions
Use cases of Biometric Authentication
Biometric technology is used by global industries such as Healthcare, Business, Education, Financial institutions, law enforcement agencies. A lot of countries are using biometrics for voter registration. Lately, the eCommerce industry is using biometrics for verifying vendors, and customers. Smart-card-based biometric authentication is said to decrease fraud by 80%. According to studies around 16,352 people fell victim to online shopping and lost £17m during lockdown amid the Pandemic. Some businesses are using voice recognition biometrics to give security services over the phone.
Similarly, banking institutions use biometrics to authenticate users better and ensure the safe flow of transactions. Biometrics is strengthening payment security. From online banking to digital wallets, biometrics technology is protecting customer’s financial assets. It not only fosters customer trust but also safeguards all or any privacy concerns. Leading global financial institutions are embracing biometric technology for customer authentication, eliminating traditional security methods, and non-compliance penalties to provide better customer experience.
The use of biometrics technology is providing a safe experience for passengers in the travel industry. Biometric technology is revolutionising the way people travel. Biometric authentication is required during the VISA application process in order to expedite the application and customer screening process consequently facilitating customer and airline security. The customer’s picture is captured by security cameras to match with the databases of suspects using facial recognition technology which can further help in tracking down terrorists and high-risk profiles through face detection.
Apart from these industries, biometric technologies are readily accepted and used by:
- Law enforcement agencies
- Voter registration
- Healthcare
- Employers/ businesses
Biometric Technology fulfilling KYC/ AML regulations
Biometric authentication is changing the customer identity verification landscape. Let’s see how this technology is influencing Know your Customer (KYC) and Anti-money laundering (AML) compliance. In this digital world, biometrics technology is a way to prevent identity theft and online fraud. This technology assists KYC and AML processes to deliver robust and intuitive identity proofing.
As more and more institutions are using identity verification protocols, KYC processes using biometrics are rapidly gaining attention as it has proven itself by delivering convenience meanwhile complying with government regulations for preventing financial crimes such as money laundering, corruption, tax evasion, terrorist financing, and identity theft.
Banks are required by the law to follow KYC and AML policies put forth by local governments. The primary aim of KYC is to protect financial systems from criminals, who otherwise may want to use the system for fraudulent activities and laundering money. Talking about the past, banks did not pay much attention to verifying customers, as a result, they were charged with heavy penalties. So in order to avoid billion-dollar fines, financial institutions are putting an end to violating KYC and anti-money laundering norms. As reported by Reuters, HSBC had to pay $1.9 billion to US authorities for allowing it to be used to launder drug money out of Mexico, at the end of 2012. According to the FTC (Federal Trade Commission), almost 9 million Americans are victimized each year due to inefficient KYC.
Complying with KYC policies means reducing financial crime risks. KYC gives you an opportunity to actually know your customers, who they are, where their income is coming from, their background data including financial portfolios, and how much risk they pose to the institution. On the other hand, Anti-money laundering regulations help with risk assessment, customer background history is thoroughly screened against government global sanctions and blacklists to identify if they were ever involved in shady or illegal activities so that the proper actions can be taken. Moreover, KYC checks enable a secure environment for investors, and through know your business (KYB) processes clients can identify the legitimacy of the company they are conducting businesses with. So, apart from preventing crimes, KYC, KYB, and AML through biometric technology build trust between the parties for successful business relationships and seamless customer onboarding.
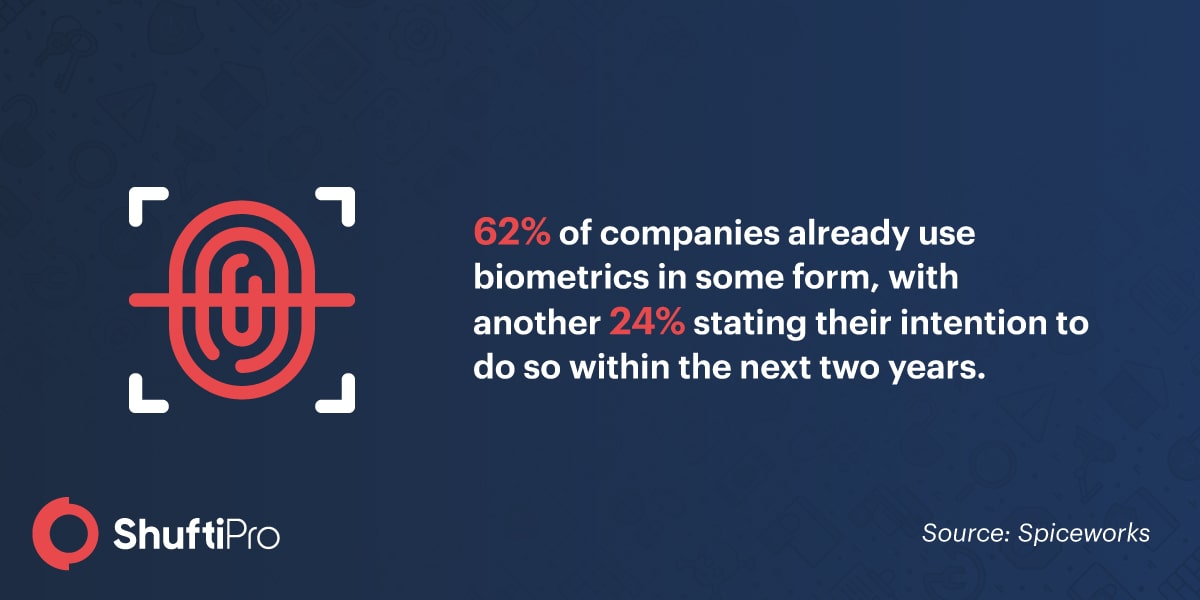
Challenges of Biometric technology
There is no doubt that biometric authentication is more important now than ever before and the adoption is becoming mainstream. Companies are adopting various techniques to identify people and assess their behavioral patterns. But by giving away your fingerprint, or your face, one is actually giving away important data that basically makes up a person’s identity. No one knows where the information goes and how it will be used. These concerns are not redundant in fact, they should be addressed in order to avoid significant future problems.
Biometric technology has a lot of benefits over traditional authentication systems but there are some risks and challenges associated with it too. It is crucial to ensure the safety of biometric data, but what if the data falls into the wrong hands? Biometrics frequently brings with it privacy and security concerns. MasterCard and HSBC are using facial recognition technology to verify the customer’s identities. Ford is partnering up with a machine vision company to add facial recognition technology to its vehicles. Even though these innovations are remarkable, all the data may give unprecedented access to bad actors. Companies are storing customer’s fingerprints, facial features and all this storage of large-scale biometric data is risky and valuable to online criminals, at the same time. The reason why some companies are adopting the token system. Using tokenization, biometric data of people aren’t stored in the same place, which makes it difficult for hackers trying to steal and misuse. Also using a combination of biometric authentication for a single customer can confuse the hackers.
Even though biometric authentication is more of a paradigm shift for businesses around the globe. But proper and secure biometric authentication is considered to be more advantageous to global companies.
Facial Biometric Verification amid Pandemic
Speaking of biometrics, contactless biometric authentication is becoming increasingly popular in times of the COVID-19 virus outbreak. WHO (World Health Organization) has demanded people to stay indoors and maintain social distance in packed places to obstruct the spread. Under such circumstances, fingerprint scanners are no longer useful since there are chances that they may carry the virus likely to transfer through physical contact. Therefore, contactless biometric technology such as facial recognition technology is making its mark.
Customer identification through facial recognition is helping companies and customers to enforce social distancing as facial biometric authentication puts an end to physical contact. Customers are seamlessly verified through face biometrics for secure and easy authorized access.

As mentioned above, businesses have seen a substantial increase in online scams and breaches in the wake of the COVID-19 pandemic. This calls for stronger customer authentication techniques and there is no other better solution than facial biometric authentication technology.
Shufti’s Facial Recognition Solution
The use of artificial intelligence and machine learning technologies makes facial recognition more accurate. Shufti’s facial recognition systems prevent businesses from spoof attacks because of its anti-spoofing techniques. It is revolutionizing the way businesses or customers access sensitive information. Facial anti-spoofing techniques help prevent fraud and reduce theft. Shufti’s AI-based anti-spoofing technology has the ability to detect and combat facial spoofing attacks through:
- 3D depth perception
- Micro expression analysis
- Liveness detection
The system uses deep learning to analyze the facial data and identify almost all kinds of facial spoofing attacks. Speaking of which, Shufti detected 42 different spoof attacks in the year 2019. Facial biometric authentication enhances security by identifying:
- 3D photo masking
- Deep fakes
- Face morphing attacks
- Forgery, and
- Photoshopped images
How does Shufti’s Facial Biometric Authentication work?
Account logins through facial biometric remove friction and delays which eases the login process while adding an extra layer of security. Shufti’s facial biometric authentication is done in 2 simple steps:
At the time of signing up, facial recognition technology ensures the live presence of the individual through liveness detection after the customer enrolls his face. The biometric markers are stored for future login attempts. The iFrame captures the video selfie of the user’s face and verifies existing presence within the system.
After the initial step, the biometric authentication service auto-extracts information from the identity document using the OCR (Optical Character Recognition) technology to ensure the user’s real identity for high-risk transactions and also to match the face with the face on the ID document by uploading an image of a valid ID card.
Ongoing KYC is performed to identify and authenticate all transactions performed by the account holder.
Shufti has recently launched its Biometric authentication SDK. Facial Biometric authentication is quickly making its way into customer identification and authentication. Manual and traditional recognition techniques are becoming redundant due to their shortcomings and lazy ways. Shufti’s facial biometric authentication is an ideal solution over traditional authentication methods for ease and convenience.

Key takeaways
Online frauds are evolving quickly and companies are facing challenges in finding or deploying more sophisticated ways to stay ahead of the curve. Biometric authentication is designed to protect systems from external threats. Password, knowledge, token, and out of band based authentication are the things of the past. Biometric authentication technology protects against frauds as it depends on biometric data unique to every individual customer. Facial biometric authentication uses an individual’s face for authentication which is one of the most secure forms of customer verification.
Shufti’s facial biometric authentication requires user’s consent as end-users are supposed to enroll their face before proceeding further. Additionally, it uses the effective techniques of liveness detection to prevent facial spoof attacks by ensuring the remote physical presence of customers in question.
Passwords are no longer considered secure in this day and age. With data breaches every day, our passwords are sold on the dark web by criminals, purchased by other criminals for malicious intent such as identity theft and account takeovers. The reason why biometric authentication is preferred by global industries for ensuring identities, better customer experience, higher conversion, and lower drop off rates.